Report that information of more than 60,000 spyware users was successfully read using SQL injection

Eric Daigle, a computer scientist and white hat hacker, has revealed in a blog post how he exploited a vulnerability in a spyware app for Android devices called 'Catwatchful' to gain access to approximately 62,000 user accounts.
Taking over 60k spyware user accounts with SQL injection :: Eric Daigle
Data breach reveals Catwatchful 'stalkerware' is spying on thousands of phones | TechCrunch
https://techcrunch.com/2025/07/02/data-breach-reveals-catwatchful-stalkerware-spying-on-thousands-android-phones/
Daigle investigated the spyware app 'Catwatchful' for Android. Catwatchful was a spyware app that purported to be a tool for monitoring children, but instead secretly collected photos, messages, location information, microphone audio, and camera footage from smartphones without permission.
Daigle noticed that in the process of creating a free trial account, user information was registered in two places: Firebase and a custom database at the domain 'catwatchful.pink.'
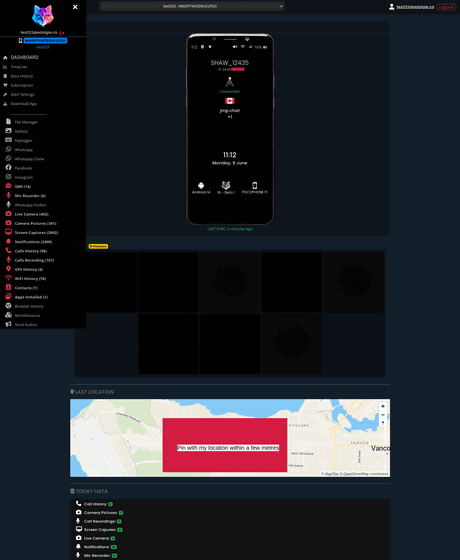
Once Catwatchful is installed, various information can be collected from the target smartphone and monitored from the control panel. Most of the collected personal data is stored in a highly secure and difficult-to-attack Firebase database. On the other hand, the API of the catwatchful.pink server can be accessed without authentication, but since it is difficult to guess the parameters that identify individuals, simple unauthorized access is difficult.
However, when they attempted to inject SQL into the 'getDevice' endpoint of this API, they found that a vulnerability in the MySQL database was easily discovered.
By exploiting this vulnerability and further investigating the database, Daigle found that a table called 'user' contained the user IDs and plaintext passwords of approximately 62,000 users of the service, as well as data on 26,000 victim devices. Daigle reports that this gave him effective control over all accounts on the service.

Most of the compromised devices were located in Mexico, Colombia, India, Peru, Argentina, Ecuador and Bolivia, with the oldest data dating back to 2018.
In addition, the database also revealed the identity of the Catwatchful administrator and developer. Daigle, in cooperation with TechCrunch, emailed the administrator asking if he was aware of the data breach that had taken place using Catwatchful and if he would notify users that their data had been exposed through a vulnerability in the database, but did not receive a response.
The web company that hosted the Catwatchful API told TechCrunch that it had suspended the spyware developer's account and temporarily blocked the spyware from functioning, but that the API was later restored on the servers of hosting provider HostGator. HostGator did not respond to a request for comment about the spyware's hosting company.

TechCrunch then reported that it provided personal information obtained from Catwatchful's database to the data breach notification service Have I Been Pwned?. It also reported details of the Firebase instance involved in storing Catwatchful's data to Google. Google responded, 'All apps that use Firebase products must comply with our terms of service and policies. We are investigating this matter and will take appropriate action if violations are found. Android users who attempt to install these apps are protected by Google Play Protect.' However, at the time of writing, Catwatchful is still hosted on Firebase.
Although the catwatchful.pink site was taken down, service was quickly restored on a different domain, with the vulnerability still present, and Daigle said the other domain had a web application firewall installed, which blocked SQL injection attacks.
Related Posts:
in Software, Web Service, Smartphone, Security, Posted by log1i_yk