"NAND mirroring" to extract data by breaking the iPhone passcode input limit can be realized

ByMarcCEcases
Entering a passcode on iPhone If the locking screen is released a predetermined number of times, the terminal will be locked and finally it will be initialized "Passcode lockA way to avoid by force technique was demonstrated. This method is to effectively invalidate passcode lock by copying the contents of the "NAND memory chip" for storage installed in the iPhone to create a clone.
Hacking the iPhone PIN retry counter | Light Blue Touchpaper
https://www.lightbluetouchpaper.org/2016/09/15/hacking-the-iphone-pin-retry-counter/
Hardware hack defeats iPhone passcode security - BBC News
http://www.bbc.com/news/technology-37407047
The riot over passcode lock of the iPhone occurred in California in 2015San Bernardino gun shooting incidentThe battle between FBI and Apple during the investigation in the country is best known. The FBI, who told Apple that important data of the incident was left on the iPhone 5c possessed by the suspects and the couple who were shot dead by shooting gun shooting incident, requested Apple to cooperate to cancel passcode. However, Apple refused this as "concerning the user's privacy."
Although it was temporarily a case of FBI vs. Apple's "passcode locking problem" developed to the lawsuit, suddenly FBI withdrew the lawsuit as "the cooperation is no longer necessary", and with the help of a third party, I succeeded in unlocking.
IPhone can unlock its own without relying on Apple, court battle is over - GIGAZINE
Although the method used by FBI and its collaborators at this time has not been clarified, the inside which is thought to be influential is copying the whole contents of the NAND memory chip storing the terminal data entirely to another chip It was what was called "NAND mirroring" that puts the same thing into the. Research papers and movies that reproduce such mirroring using the real machine of the iPhone are released.
[1609.04327] The bumpy road towards iPhone 5c NAND mirroring
http://arxiv.org/abs/1609.04327
Dr. Sergei Skorobogatov of Cornell University who conducted this research first removes the logic board from the experimental iPhone 5s, exposes the chip by removing the covers. The target NAND memory chip is mounted on just the back of the A6 chip.

Where the chip was exposed, he heated the entire board using an electronic heat gun, melted the solder and removed the chip from the board. If this work fails, there is a possibility of destroying the board and the chip itself, so high technology is required.

Next, in order to check whether the removed NAND memory works properly, Dr. soldered the chip and board terminals with cables and confirmed the operation.

Although it seems there was a trouble such as power supply does not work properly on the way, I was able to confirm that it works safely. As a result, we confirmed that the iPhone operates even when the NAND memory is put out.

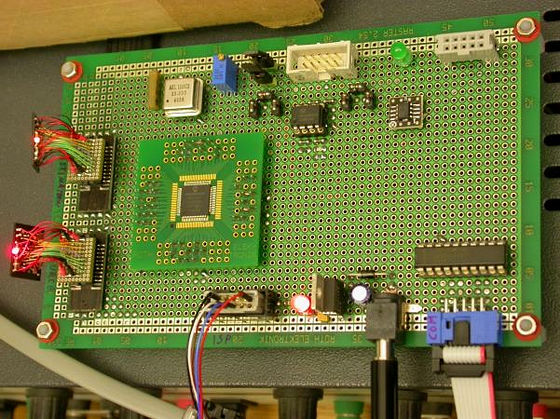
Dr. who confirmed the operation installed a board on the back of the iPhone and equipped with a connector so that NAND memory chip can be easily replaced. However, in this state, even if I loaded the NAND memory chip and booted iPhone, it did not work well. As a result of the analysis using the oscilloscope, it turned out that the resistance value (impedance) changed due to the cable becoming longer, the waveform of the signal was distorted (distorted), and the data could not be exchanged successfully That's right.

Therefore, in order to solve the impedance problem, Dr. equipped "buffer circuit" which stabilizes the signal on a large board (photo right). This solves the problem and it seems that the iPhone works properly. Also, at this stage, we are introducing a "Logic Analyzer" (photo left) that logs data and deciphers proprietary protocol used for interaction between logic board and NAND memory chip.

And on the PC side, we have created a device for mirroring NAND memory chips.
By making full use of such equipment, Dr. Succeeded to effectively invalidate iPhone's passcode lock. The situation is contained in the following movie.
Demonstration of iPhone 5c NAND mirroring - YouTube
I prepared iPhone 5c for experiments and a device that mirrors the aforementioned NAND memory chip.

IPhone has been remodeled so that NAND memory chip can be freely removed. Remove the tip ......

Attach it to the mirroring device.

In this state, turn on the device and operate the PC, the data contained in the NAND memory chip is sucked out and copied (mirrored) to another NAND memory chip mounted in the device. The actual turnaround time will take about an hour and a half.

When mirroring is completed, insert the chip on the iPhone ......

Successful if booting starts.

Enter the passcode required at startup. In the movie, tried unlocking by inserting a number in order from "0000" as a trial. However, when entering the sixth "0006" ... ...

The terminal was locked. When iPhone fails to enter passcode 10 times, the terminal is completely initialized. It is said that this device was made to avoid this, but if it is said method ...

Remove the NAND memory chip from the iPhone and replace it with another NAND memory chip. In this NAND memory chip,Exactly the same contents as the first chip are written.

Boot with the chip attached. And if you try passcode again from "0007", it is a power technique that one day you can reach the passcode of the correct answer, but the validity of a certain method has been confirmed.

If we do pass code corruption in this way, we can reach the correct passcode at several days level. However, it seems that it will take more time if the passcode is 6 digits or including alphabet.
Related Posts: