An attack method to steal Apple ID by continuously sending identity verification notifications to iPhone is reported

The existence of an attack method that steals the Apple ID by continuously sending notifications to the iPhone requesting to reset the Apple ID password has been confirmed. The attacker is also said to be using a 'phone masquerading as Apple official support.'
Recent 'MFA Bombing' Attacks Targeting Apple Users – Krebs on Security
Last night, I was targeted for a sophisticated phishing attack on my Apple ID.
— Parth (@parth220_) March 23, 2024
This was a high effort concentrated attempt at me.
Other founders are being targeted by the same group/attack, so I'm sharing what happened for visibility.
???? Here's how it went down:
If you forget your Apple ID password, you can request a password reset from the password reset page . To reset your password, you must enter your email address and phone number on the reset page, and select 'Allow' in the password reset notification sent to your Apple device. Additionally, if the notification appears, the notification will not disappear and you will not be able to operate the device until you tap either 'Don't Allow' or 'Allow'.
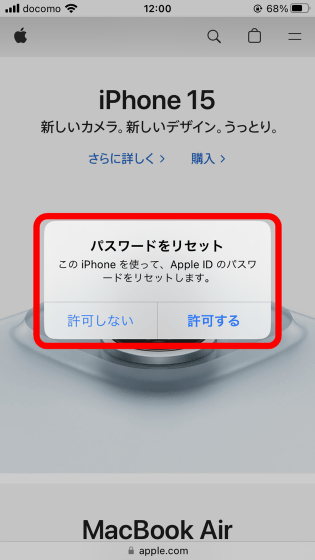
According to a damage report posted by X user Parth, at around 6:36 pm on March 23, 2024, Parth received over 100 notifications requesting permission to reset his password on all Apple devices he owns. He said. Even if you tap 'Don't allow,' the next notification is displayed immediately, leaving Parth unable to use his iPhone or MacBook.
The attackers made a led high effort focused attack on me, using OSINT data from People Data Labs and caller ID spoofing.
— Parth (@parth220_) March 23, 2024
First, around 6:36pm yesterday all of my Apple devices started blowing up with Reset Password notifications.
Because these are Apple system level alerts,… pic.twitter.com/vX1AZvoVoN
Furthermore, about 15 minutes after the notifications were sent consecutively, he received a call from a person claiming to be an official Apple supporter. Mr. Parth became suspicious and asked the person on the other end of the call to provide ``Mr. Parth's personal information that Apple's official support should know,'' but the person on the other end of the line confirmed Mr. Parth's date of birth, email address, and phone number. I correctly guessed the number, address, and past addresses.
About 15 minutes later, they call me on my number, using Caller ID spoofing of the official Apple Support phone line (1 (800) 275-2273).
— Parth (@parth220_) March 23, 2024
They really emphasized this detail to win trust from the victim.
I was obviously still on guard, so I asked them to validate a ton of… pic.twitter.com/Xi12VzrNy5
However, the person on the other end of the call mistakenly recognized Mr. Parth's name as ``Anthony.'' In fact, Mr. Parth's personal information was registered with a personal information service called People Data Labs with the wrong name and occupation, and the person on the other end of the call answered the wrong name based on the information from People Data Labs. That's what happened. Because Parth happened to know that his information had been incorrectly registered with People Data Labs, he was able to realize that the person on the other end of the call was a fraudster posing as an official Apple support representative.
Thankfully I was tipped off that they used my data from People Data Labs in real time to validate a ton of information.
— Parth (@parth220_) March 23, 2024
Despite correctly all stating of my data, the phishers thought my name was Anthony S.
????????????????????????
The reason I caught it is because, I've queried myself on… pic.twitter.com/dUMitmphKS
The person on the other end of the call eventually asked for a one-time password, but Parth, who was convinced it was a scam, succeeded in avoiding damage.
Mr. Parth was lucky to be able to prevent the theft of his Apple ID, but if he took one of the following actions: ``Tap 'Allow' on the password reset notification'' or ``Give the one-time password'', the attacker could Your Apple ID will be hijacked by someone else. Additionally, in Mr. Parth's case, the attacker used a two-stage attack method: ``continuous notifications'' and ``phone calls pretending to be from Apple official support.'' According to security expert Brian Krebs, There have also been reports of cases where only 'continuous transmission of' is executed.
Mr. Krebs points out that there is also a problem with Apple's system that can send password reset confirmation notifications continuously.
Related Posts:







